Email and File Encryption
📧 Fortifying Your Inbox: A Real-World Use Case for GPG Email and File Encryption
Section titled “📧 Fortifying Your Inbox: A Real-World Use Case for GPG Email and File Encryption”In an era where data breaches are daily news and privacy is increasingly under siege, relying solely on your email provider’s security can be a gamble. While transport-layer security (TLS) encrypts your email in transit, it doesn’t protect the message once it lands on the recipient’s server—or if their provider is compromised.
This is where GPG (GNU Privacy Guard) steps in. GPG is the free and open-source implementation of the OpenPGP standard, providing a robust, end-to-end encryption solution. It uses public-key cryptography, ensuring that only the intended recipient can decrypt and read your messages or files.
Here is a compelling, real-world use case that demonstrates the critical value of GPG encryption for both email text and attached files.
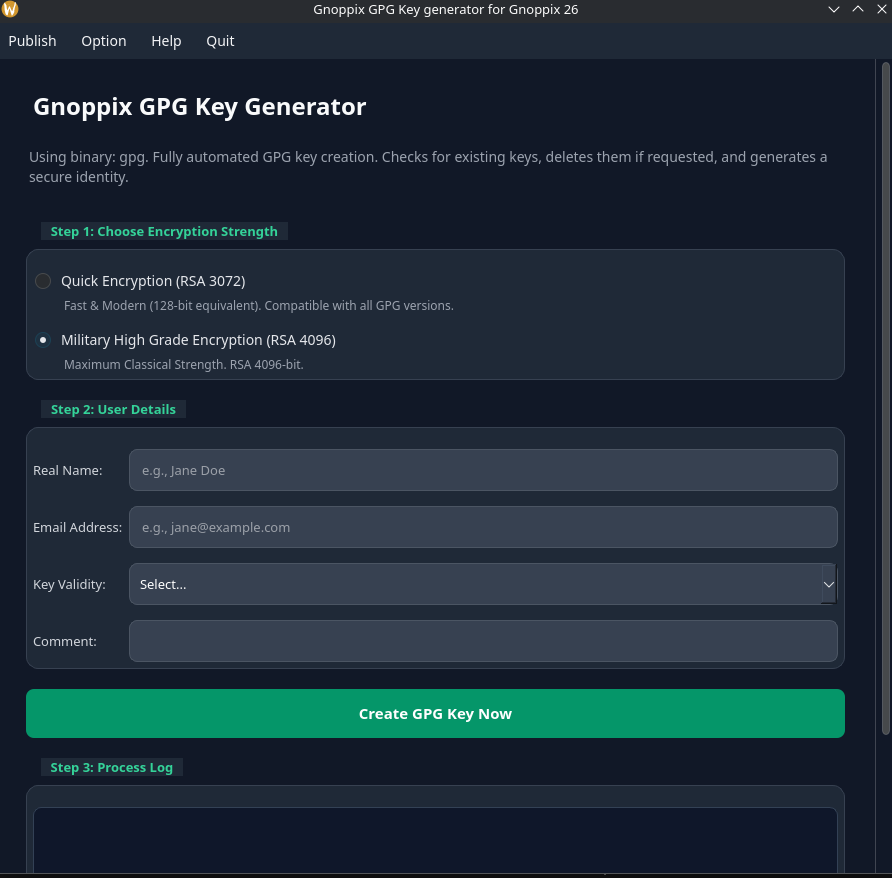
🛡️ The Use Case: The Freelance Finance Consultant
Section titled “🛡️ The Use Case: The Freelance Finance Consultant”Meet Alice, a self-employed financial consultant who regularly handles highly sensitive information for her clients: tax documents, investment reports, bank statements, and proprietary business plans.
The Security Challenge
Section titled “The Security Challenge”Alice’s typical workflow involves:
- Emailing highly detailed, private financial reports to her clients.
- Receiving scans of personal tax documents (e.g., W-2s, 1099s) as PDF attachments.
- Sending contract drafts that contain confidential clauses and pricing.
If Alice or her clients relied on standard email, all this sensitive data would sit unencrypted on their respective email servers. A server breach, a weak password leading to an account takeover, or even a targeted phishing attack could expose every piece of her clients’ financial lives. The legal and reputational damage would be catastrophic.
The GPG Solution
Section titled “The GPG Solution”Alice implements GPG encryption across her entire professional communication stack:
1. Encrypting the Email Text (End-to-End Confidentiality)
Before sending a sensitive email, Alice uses a GPG plugin in her email client (like Thunderbird with Enigmail or a dedicated GPG suite) to encrypt the message body using her client’s public key.
[Image of the GPG encryption process: A simplified diagram showing Alice encrypting a message with Bob’s public key, the ciphertext being sent, and Bob decrypting it with his private key.]
- How it protects: The resulting email is just an unintelligible block of characters (ciphertext). If a hacker intercepts the email or breaks into the server, they see only gibberish. Only the intended client, who possesses the matching private key, can decrypt and read the message.
2. Encrypting Attached Files (Securing Documents)
Instead of sending unencrypted PDF or spreadsheet attachments, Alice uses GPG to encrypt the files before attaching them to the email.
- How it protects: She can use GPG to encrypt the files with the client’s public key, or, for an extra layer of security, use a symmetric encryption method within GPG and share the passphrase through a secure, non-email channel (like a secure chat app). This ensures that the sensitive document is protected even if the email and the email server are compromised.
3. Digital Signatures (Authentication and Integrity)
Alice also uses her private key to attach a digital signature to every email she sends.
- How it protects: This signature serves two crucial functions:
- Authentication: It verifies to the client that the email genuinely came from Alice and not an impostor (a phishing attempt).
- Integrity: It guarantees that the message or file has not been tampered with in transit. If even one character is altered, the signature validation will fail.
The Unbreakable Benefits
Section titled “The Unbreakable Benefits”By implementing GPG, Alice transforms her communications from a security liability into a competitive asset:
- Zero-Knowledge Security: Neither Alice’s email provider nor her client’s provider can read the contents of the messages.
- Regulatory Compliance: It helps her meet stringent data privacy regulations like GDPR, HIPAA (if applicable to financial data), and various state laws by ensuring data is encrypted at rest and in transit.
- Client Trust: She can confidently assure clients that their most private data is handled with the highest level of cryptographic security, fostering deeper trust and professionalism.
GPG is not just for whistleblowers and journalists; it is a vital tool for any professional—consultant, lawyer, healthcare worker, or small business owner—who handles private data and values the trust of their clients. It is the gold standard for taking back control of your digital privacy.
Would you like a step-by-step guide on how to set up GPG on a specific operating system, such as Windows, macOS, or Linux?